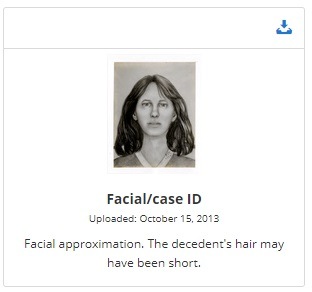
In The Blood: DNA testing truly is a complex and, for many, controversial topic area, set against a backdrop of global differences in approach to fundamental rights and freedoms which can make discussions like this too hot to touch. Nonetheless, there are still these much bigger discussions to be had around the way we use the power of DNA to prevent harm in society and that’s the real challenge here – getting to a point where the basic premise of the discussion is understood in its simplest form: a problem to solve. For me the conversation starts with that poor girl in the field. She deserves to be known. She deserves peace. In a world where her DNA was attributable to her, nearly forty years wouldn’t have passed. But sometimes solving one problem can create many more conflicts and it is important to appreciate that fully. This is the thing about investigative work. Sometimes, there’s just no easy answer. But we still have to talk about even the things we might not want to, calmly and rationally, because an unexplored avenue might be the one where the right answer lies.



Responses